How to Evaluate Your IT Systems
By Chris Morino
Bonus: FREE Template
Technology is a significant component of all businesses, and it’s in your best interest that your IT systems serve your business interests. Rather than reacting to technology issues as they crop up, you can build a comprehensive IT plan that leverages technology so your team can meet business objectives. And it all starts with evaluating your IT systems.
That being said, evaluating your IT systems can be tricky, which is why we have developed a template to help.
In this post, we’ll be discussing how to evaluate your IT systems, the tools you can use to assess your performance, and some key business objectives you should monitor regularly.
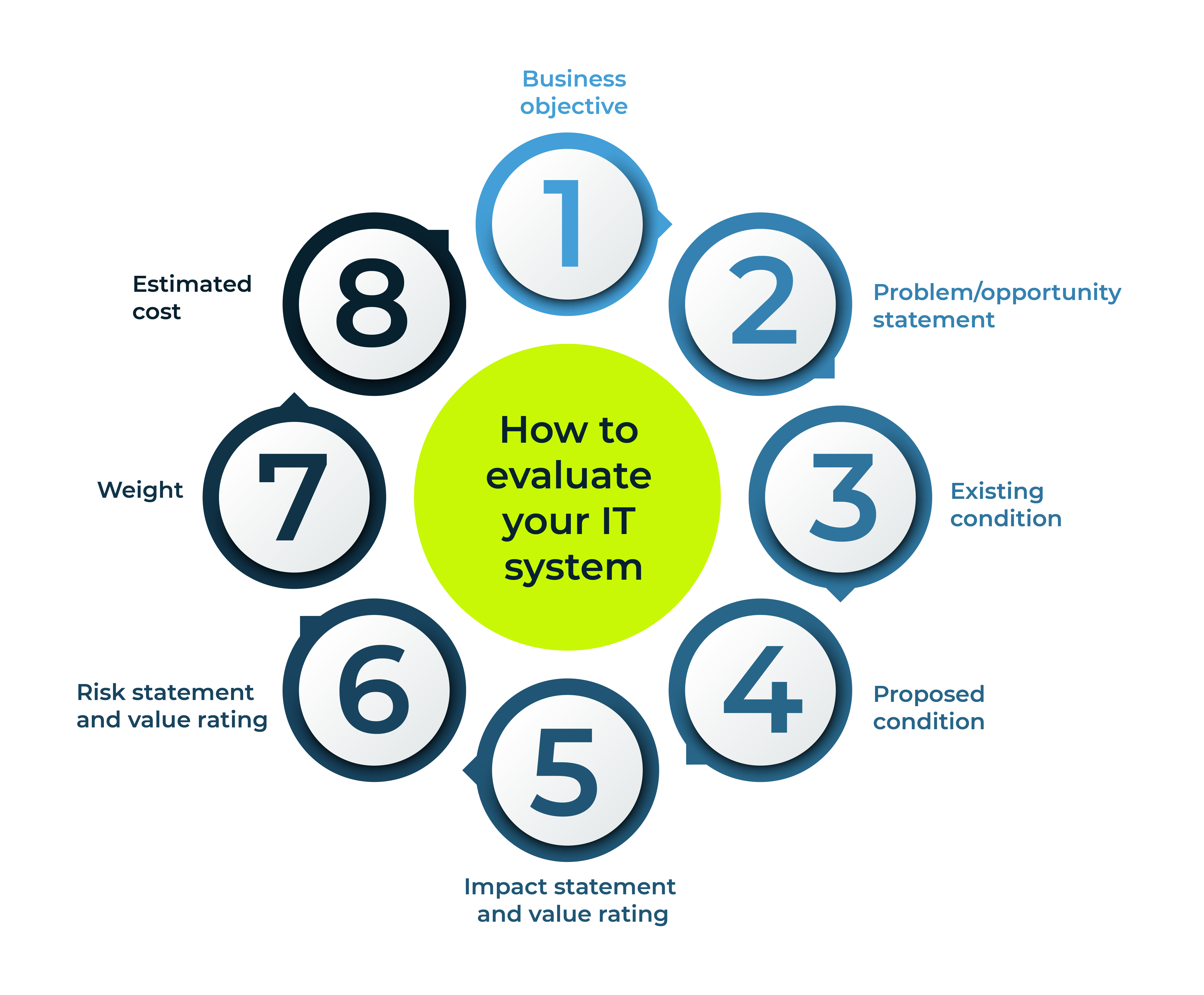
Evaluation metrics you should use
These eight evaluation metrics are tried and true ways to develop the best IT solutions for your business, which is why we created a template to outline how to utilise them.
1. Business objective
Ask yourself: What goal is your business working towards?
Your IT goals should be aligned with the overall business goals so that your IT systems can play a central role in your processes and proactively support growth.
Many businesses’ IT systems are purely reactionary; when something breaks down or stops working, IT works on it and then waits for another intervention. What happens in this scenario? The IT department cannot work on larger objectives or goals to make technology work for your business for increased efficiency.
When you begin your evaluation, it is essential to do it with proactive goals in mind—you want IT systems that best utilise your resources and improve return on investment (ROI).
2. Problem/opportunity statement
Ask yourself: What are you trying to solve or improve by implementing this business objective?
This statement will address the issue at hand. Whether trying to solve a problem or build new growth opportunities, this statement will elaborate on why you are working towards this objective in one to two sentences.
3. Existing condition
Ask yourself: How are things going right now?
This statement will describe the current state of your IT systems—it’s a high-level look at your existing systems, going over what is going well and what you'd like to improve. If you have tried other initiatives in the past to accomplish a similar goal, you should name them here.
4. Proposed condition
Ask yourself: Where do you want to be?
Your proposed condition describes your ideal solution. This section briefly describes what you could accomplish with the suitable IT systems in place and how they lead to your business goals. Your business should take this opportunity to list specific initiatives or technology improvements that would help accomplish these goals.
5. Impact statement and value rating
Ask yourself: How will these actions impact your business operations?
Your impact statement describes the value of moving forward with the current plans. Not only should you provide a comment here, but we also recommend ranking it on a scale from 1 to 10, with 10 being the highest. This evaluation will help indicate the value of the improvements at hand.
6. Risk statement and value rating
Ask yourself: If you do not complete this business objective, what risk does this pose for your company?
Whether struggling with outdated technology or the risk of specific software becoming obsolete, you should also state any possible risks to your company by not following these initiatives.
On the other hand, you can also list the side effects that might show up if you complete the work; for example, a less productive quarter as employees learn new software. Score the risk value on a scale from 1 to 10 to better quantify the benefits and risks of your IT initiatives.
7. Weight
Ask yourself: How should I prioritise these initiatives?
To calculate, try this simple formula: Weight = Impact × Risk.
While your evaluation may uncover several things you want to improve or fix, you need to prioritise them based on the risks and rewards of every business opportunity. This is what makes quantifying the risk and impact statements so important. Multiply the impact value and risk value (on a scale from one to ten) to calculate the weight of each project.
8. Estimated cost
Ask yourself: How much will it cost to do this?
Looking into potential solutions can help you estimate the cost of undertaking these projects. While some projects may have higher priority than others, you should find business objectives within your budget and have a relatively high weight.
Key business objectives you should include
1. Reducing insurance premiums
Insurance costs can add up quickly, but you can keep expenses under control by implementing certain security features to make your business more attractive to insurers. While it costs money to improve IT security, your business can save on insurance premiums and minimise security risks in the long run.
2. Better visibility into performance metrics across the company
It can take too much time and human resources to collect performance metrics company-wide and across multiple platforms or locations. By utilising the right IT tools, your company can have more automated reporting, allowing managers to spend more time on other priorities.
3. Creating a remote-work first environment
The pandemic has increased the demand for remote workplaces, and this trend seems to be here to stay even in the post-pandemic era. You want to invest in IT training and state-of-the-art equipment to increase efficiency and enable effective communication between team members in remote positions.
There you have it! Use these metrics to evaluate your IT systems and consolidate the basis for a company where technology works for you and your customers.
Ready to get started?




